Camera ZOOM FX v5.0.0
Requirements: 1.6+
Overview: The most advanced camera for Android!

>> “The
Best Camera App for Android” – lifehacker
>> “The 15
Best Mobile Apps of 2011″ – Mashable
BUY NOW BEFORE THE PRICE GOES UP! (Normal price $4.99)
★★★★★★★★★★★★★★★★
Over half a million sold!!!
OTHER REVIEWS:
“grab this to show off to your Apple-loving buddies” – SlashGear
“fun filters, zooming, timer and even image stabilisation” – Gizmodo
“Few apps offer as many options for shooting as this one” – WIRED
★★★★★★★★★★★★★★★★★★
The award-winning camera app for Android devices!
Camera ZOOM FX is now Editor’s Choice on Lifehacker, Gizmodo, Mashable and SlashGear. Over 400,000 users around the world are now using Camera ZOOM FX daily.
Blazingly fast performance: over 90 effects render instantly on your device!
POWERFUL CAMERA:
● Optical / digital zoom (up to 6x)
● Flash (if avail)
● Front facing camera (if avail)
● Customization of ALL hardware buttons
- e.g. volume buttons to control zoom, trackball to snap shot…
● Live previews of some effects, e.g. frames, buddies
● Silent camera (if device supports)
● Tweak hardware options: autofocus, whitebalance, nightshot…
● Send, share your shots
● 1-click upload photo to Facebook, Twitter, Flickr, etc. – ALL AT ONCE!
● Customizable grid overlays
● NEW!! Live Wallpaper – now “Photo FX Live Wallpaper” app
MULTIPLE SHOOTING MODES:
● Stable S on-screen meter to show current level of movement
● Timer
● Voice Activated: take a picture by clapping, shouting…
● Burst Mode
● Collage
● Time Lapse
IMPORT YOUR EXISTING PHOTOS:
● You can import existing photos from your phone’s gallery by clicking Menu->Import.
POST PROCESSING:
● Combine effects using non-destructive editing
● Process at full camera resolution (up to 8mp if avail)
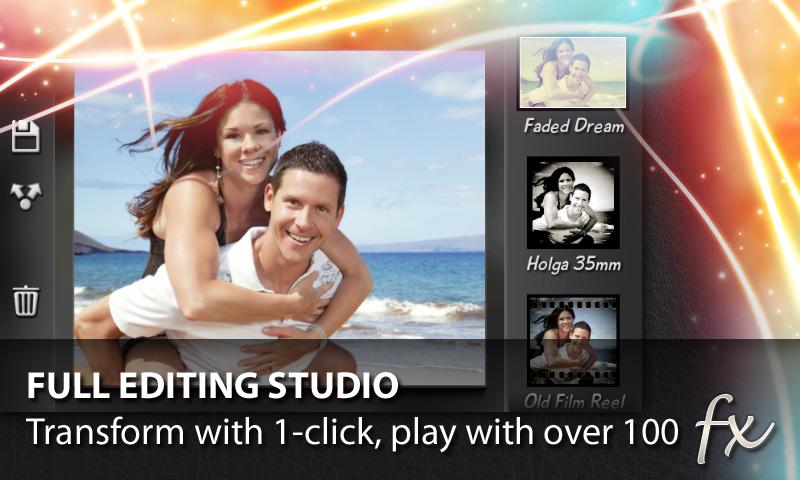
● 10 ready made presets: Diana, Retro, Holga 35mm, Toy Camera…
● 20 Color FX: vintage, lomo, cinematic, funky, pencil…
● 13 Frames: thin, rounded, lens, polaroid, filmreel…
● 6 Vignette Surrounds: heavy, invert, spotlight…
● 12 Distort FX: fisheye (like fxcamera), mosaic, twirl…
● 9 Mirror FX
● 3 Tilt-shift FX
● Crop to any size of your choice: 3×8, square, instant, 6×4…
● Digi composites (photoshop style overlays)
● Props and famous ‘buddies’ in your pictures (move and resize!)
● Create stunning collages: e.g. 2×2 passport style combination shots
● Random effects
OTHER FEATURES:
● Fullscreen shutter: click anywhere on screen to shoot!
● Animated shutter effect
● Support geotag / exif tags
● Select sdcard folder to save photos (incl external sd)
● Auto save shots
● Win $100 in Instagram style photo contest
● Pro scene modes, e.g. nightshot, beach (Droid only)
● View last shot in picture gallery
● Use as default camera
● Rotate / crop photos
● Widescreen lens / capture (if device supports)
● Support from Android 1.5 through to Android 4.0 (incl tablets)
What’s New
Camera ZOOM FX v5.0.0
Requirements: 1.6+
Overview: The most advanced camera for Android!


>> “The
Best Camera App for Android” – lifehacker
>> “The 15
Best Mobile Apps of 2011″ – Mashable
BUY NOW BEFORE THE PRICE GOES UP! (Normal price $4.99)
★★★★★★★★★★★★★★★★
Over half a million sold!!!
OTHER REVIEWS:
“grab this to show off to your Apple-loving buddies” – SlashGear
“fun filters, zooming, timer and even image stabilisation” – Gizmodo
“Few apps offer as many options for shooting as this one” – WIRED
★★★★★★★★★★★★★★★★★★
The award-winning camera app for Android devices!
Camera ZOOM FX is now Editor’s Choice on Lifehacker, Gizmodo, Mashable and SlashGear. Over 400,000 users around the world are now using Camera ZOOM FX daily.
Blazingly fast performance: over 90 effects render instantly on your device!
POWERFUL CAMERA:
● Optical / digital zoom (up to 6x)
● Flash (if avail)
● Front facing camera (if avail)
● Customization of ALL hardware buttons
- e.g. volume buttons to control zoom, trackball to snap shot…
● Live previews of some effects, e.g. frames, buddies
● Silent camera (if device supports)
● Tweak hardware options: autofocus, whitebalance, nightshot…
● Send, share your shots
● 1-click upload photo to Facebook, Twitter, Flickr, etc. – ALL AT ONCE!
● Customizable grid overlays
● NEW!! Live Wallpaper – now “Photo FX Live Wallpaper” app
MULTIPLE SHOOTING MODES:
● Stable S on-screen meter to show current level of movement
● Timer
● Voice Activated: take a picture by clapping, shouting…
● Burst Mode
● Collage
● Time Lapse
IMPORT YOUR EXISTING PHOTOS:
● You can import existing photos from your phone’s gallery by clicking Menu->Import.
POST PROCESSING:
● Combine effects using non-destructive editing
● Process at full camera resolution (up to 8mp if avail)
● 10 ready made presets: Diana, Retro, Holga 35mm, Toy Camera…
● 20 Color FX: vintage, lomo, cinematic, funky, pencil…
● 13 Frames: thin, rounded, lens, polaroid, filmreel…
● 6 Vignette Surrounds: heavy, invert, spotlight…
● 12 Distort FX: fisheye (like fxcamera), mosaic, twirl…
● 9 Mirror FX
● 3 Tilt-shift FX
● Crop to any size of your choice: 3×8, square, instant, 6×4…
● Digi composites (photoshop style overlays)
● Props and famous ‘buddies’ in your pictures (move and resize!)
● Create stunning collages: e.g. 2×2 passport style combination shots
● Random effects
OTHER FEATURES:
● Fullscreen shutter: click anywhere on screen to shoot!
● Animated shutter effect
● Support geotag / exif tags
● Select sdcard folder to save photos (incl external sd)
● Auto save shots
● Win $100 in Instagram style photo contest
● Pro scene modes, e.g. nightshot, beach (Droid only)
● View last shot in picture gallery
● Use as default camera
● Rotate / crop photos
● Widescreen lens / capture (if device supports)
● Support from Android 1.5 through to Android 4.0 (incl tablets)
What’s New
- introducing ‘Best Photo Mode’ !!
- take up to 50 shots in burst mode, and let Camera ZOOM FX decide which is the best, or choose for yourself!
- color splash effect
- all effects customisable
- new burst mode – Hold shutter to start burst, release to end
- supports HD and interval selection
- remember last shooting mode
- manual crop
- new filters: Ghostly Glow, Comic Strip
- set custom filenames for photos
- optimized for Nexus 5 / Kitkat
- much more!
https://play.google.com/store/apps/details?id=slide.cameraZoom- introducing ‘Best Photo Mode’ !!
- take up to 50 shots in burst mode, and let Camera ZOOM FX decide which is the best, or choose for yourself!
- color splash effect
- all effects customisable
- new burst mode – Hold shutter
to start burst, release to end
- supports HD and interval selection
- remember last shooting mode
- manual crop
- new filters: Ghostly Glow, Comic Strip
- set custom filenames for photos
- optimized for Nexus 5 / Kitkat
- much more!









